VPN and Secure Access requirements in ISO 27001:2022
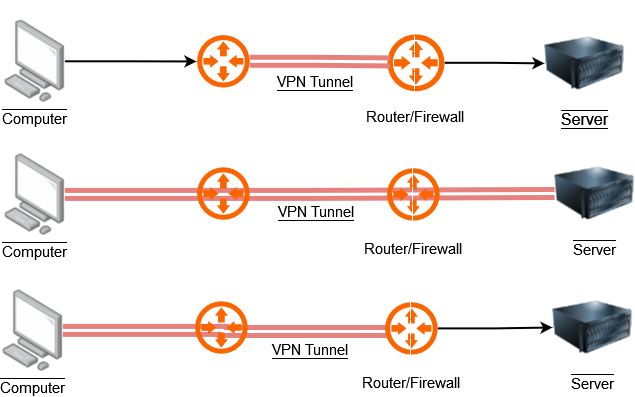

A Virtual Private Network (VPN) connection is a a communication technology that allows to create a secure and encrypted connection over a less secure network, such as the internet. This helps to protect data while connecting to enterprise resources. A VPN connection creates a tunnel from either a host or a router to another host a router.
The main benefits of Using a VPN are:
- Access internal resources: A VPN can be used to access company resources that are usually only available from inside the network perimeter of the company.
- Privacy: A VPN helps protect your online privacy by hiding your IP address and encrypting your internet traffic.
- Security: It provides a secure connection when using public Wi-Fi or other unsecured networks, protecting your data from potential threats.
- Access: VPNs can help you bypass geo-restrictions and censorship, allowing you to access content that may be blocked in your region.
- Anonymity: By masking your IP address, a VPN helps maintain your anonymity online.
VPNs are widely used by individuals and organizations to ensure secure and private communications. They're particularly useful for remote work, protecting sensitive information, and accessing restricted content.
ISO 27001:2022 addresses VPN requirements under 'Annex A, Control 6.7: Remote Working'. It addresses the following:
1. VPN Usage: Organizations should implement mandatory VPN usage policies for remote access. This ensures that all data transmitted between remote devices and the organization's network is encrypted and secure.
2. End-to-End Encryption: VPNs should provide end-to-end encryption to protect the confidentiality and integrity of data.
3. Remote Working Policy: Establish a clear remote working policy that includes guidelines for using VPNs and other security measures.
By following these requirements, organizations can mitigate the risks associated with remote working and ensure that their information remains secure. But vulnerabilities in Firewalls can be exploited by threat actors in order to have an unauthorised access to company resources. This is why many companies prefer to use other types of technologies to provide access to external parties and remote workers such as using a remote access software.
A remote access software allows for the following features:
- Remote Desktop Control: Allows users to see and interact with a remote computer's desktop as if they were sitting in front of it. This includes using applications, managing files, and performing administrative tasks.
- File Transfer: Provides the ability to transfer files between the local and remote systems, making it easier to share documents and resources.
- Security: Implement robust security measures, such as encryption, multi-factor authentication (MFA), and access controls to protect data and prevent unauthorized access.
- Session Recording: Some solutions offer the capability to record remote sessions for auditing, training, or compliance purposes.
Do you want to make sure that your information security policies and business processes are stopping attackers from accessing your company resources? Please reach out to us via the following email to learn more on how we can help your business stay secure: contact@certifymyisms.com.
Did you know: That we use Artificial Intelligence in our internal processes in order to minimize the time to getting you as secure as possible before your next audit?